


About MediaChance
Products
Links
Mediachance Newsletter
Get notified about our latest news, releases and discount offers.

MediaCryptor
Password Protect VIDEOS, IMAGES, AUDIO and DOCUMENTS
Guide
MediaCryptor PRO 3


$29
$19

MediaCryptor uses secure multi-level encryption with random IV generator. As with other modern encryption the password cannot be recovered from the data itself.
MediaCryptor encrypted files will look like a random noise in a binary editor, the files do not have any header or any recognizable pattern.
If you encrypt two exact copies of the same file with the exact same password, both of the encrypted files will be 100% different from each other - this is how
modern random seeded high quality encryption works these days.
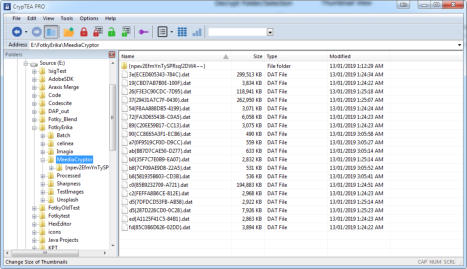
MediaCrypt works like a File Explorer with file and thumbnail views.
Encrypting and Decrypting files is easy. You can do it on the whole folder with subfolders or only on selected items. The idea of MediaCryptor is of course that you
don’t need to constantly decrypt media files if you just want to view them, because you can do so directly from their encrypted state after you enter your password.
(Formerly CrypTEA)
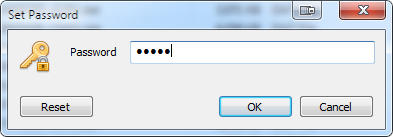
As with a file explorer you see list of files and folders. To see the encrypted files real names, you need to enter the password. The password will reveal only the files
that were protected using that password. Wrong password will not tell you that it is wrong - this feature is called a plausible deniability. It is simply impossible to
prove that any file is encrypted or just a file with random data unless you enter the correct password.


Encrypting Files
You can select to encrypt a whole folder or just a selection of files.

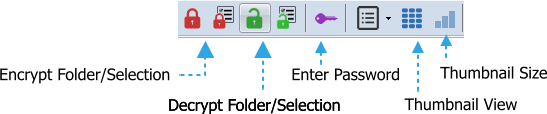
Encrypt Folder
Encrypt Selection
Recursive from this folder - all files and the subfolders in this folder will be encrypted
Remember Password until quit - the encrypted folder will remain unlocked
Encrypt/Obfuscate Folder names - the subfolders names will be encrypted as well. Unlike
the file name encryption - encrypting folder names uses a much weaker encryption
Verify Encrypted Files - the file will be after encryption decrypted and compared with the
original. Normally it is not needed.
Use Secure Delete - The original files will be scrubbed (overwritten, then deleted) instead
of just deleted.
Add Recovery Record - a small parity record will be attached to the file which may help
with recovery in case of disk failure. See Note 1.
Keep Original File Date Attribute - encrypted file keeps the same date attributes like
original file
Fully Randomly Generated file names - the file names of encrypted file will be
completely random. If this option is OFF the file names will be pseudo-random. See Note 2.
Note 1: A common risk of any encrypted files (and also any compressed files such as zip or rar) is their higher vulnerability to transmission or disk errors and
corruptions. A single flipped bit somewhere inside encrypted file means the file can’t be decrypted or decompressed at all.
We added an optional recovery block option that can be added to each of the encrypted file. If the file gets partially damaged because of the transmission or disk
error there is a good chance the file can be restored back to the original encrypted state. This has little overhead as the recovery is set to be less than 1% of
encrypted data. This is usually enough to recover from most probable failures that spans across few disc sectors.
The recovery record has no security risks because it is generated from the ENCRYPTED data. That means a damaged encrypted file can be recovered only into
undamaged but still encrypted file. You will still need the password to decrypt it.
It is of course debatable if attaching recovery option is entirely needed. The best practice would be to have full backup of important data and not relying on file
recovery. Most disk failures these days are either recoverable or complete catastrophic and very little in between.
Note 2: By default each time you encrypt a file, it will be generated with a fully randomized encrypted file name, each time different. That increases security and it
also means you can have encrypted multiple versions of the same file.
This may not be desired if you use files for a backup in Cloud where you may want the newly encrypted file to overwrite the old one or else you will soon run out of
space by adding duplicate files. For this reason you can switch this option OFF. The file name generator will be then seeded from the original file name and it will
simply result in generating the same encrypted file name every time. There is no actual reversible relationship between the encrypted file names and the original file
name - the pseudo random option only makes sure the file name will be random but always the same for that file.
Animated Video Thumbnails
In version 3 we added option to generate Animated Video Thumbnails for an easy preview of encrypted video files in thumbnail browser. These thumbnails will be
generated as a short animated GIFs (named *.vgif) encrypted with the video and then also appear in the Thumbnail view.
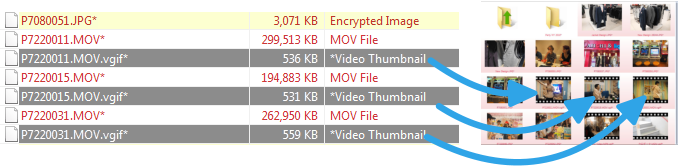
Generating video thumbnails can be done before or after
encryption. If thumbnail is generated from encrypted file, it will
be also automatically encrypted using the same password.
Clicking on the animated thumbnail will open the actual video in
the internal video player.
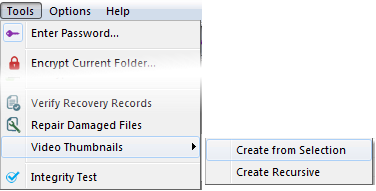
To generate thumbnails you have two options. One is to let MediaCrypt to automatically generate thumbnail from the files using menu Tools->Video Thumbnails or
generate a thumbnail from a certain place in the video manually from within the video player.
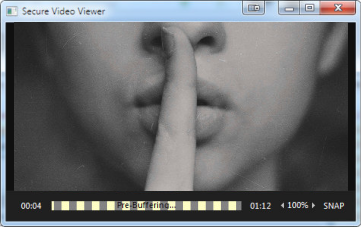

OR
Pressing SNAP during playback in
video player will generate animated
thumbnail from the current place in
video
There are few settings in the Options->Settings dialog related to the video thumbnails:
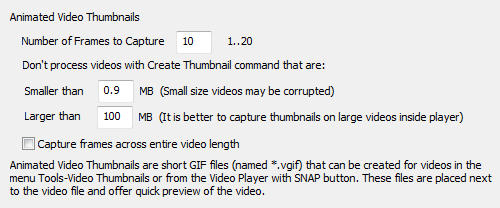
The Length of the animated gif loop is set by the number of frames to capture. Usual
good number is about 10 which results in few seconds of low FPS animation.
There are limits you can set for the minimum and maximum size of video that will be
precessed in the Tools->Video Thumbnails option. This is done mostly for protection - a
very small size video could mean it is a corrupted file and a very large encrypted videos
will take long time to process. You can always make thumbnails for those excluded
videos manually in the video player.
Capture frames across entire video - the set number of frames for the animated gif will
be captured from various places across entire video resulting in a snapshot of the video
over time. If OFF (default) it will result in a short video from beginning of the file.
Using this option may be bit risky if your video files may be corrupted (various
downloaded web videos etc..) and seeking within such file may crash the video player.
Processing multiple (or all)
video files at a time
Notes about Encryption
The encryption advanced rapidly over last decades and most of the currently used non-symmetrical standard algorithms are considered far stronger than any of
the content people may try to encrypt does require. Breaking encryption is not your primary concern and it is usually reserved for academic discussion. The
password is where the vulnerability is. If it can be guessed, brute forced or simply threaten you to reveal it then even the strongest encryption in the world will
be useless.
A good solution is to use plausible deniability type encryption such as MediaCryptor that produce files that are impossibly to determine if they are encrypted or not
even in the same software that encrypt them.
Consider two files: “secure-bank-details.xls.enc” and “90{CC8E65A3F1-ECB6}.dat”. You may know both are encrypted but in the first case everybody else who
looks at your files (including malware) will know that as well and also that the file is probably very important to you because you bothered to encrypt it. In the
second case only you know that the file contains secrets.
Mediacrypt doesn’t know if the file 90{CC8E65A3F1-ECB6}.dat is encrypted or not unless you supply a password that in fact decrypt it into something usable. If
you use incorrect password then there is no such thing as “password error” because again, it may just be a random dat file that you are trying to decrypt. Who
knows, only you know for sure.
It is important to mention that one exception is encrypting the Folder Names. Because of them having small sample data (there is nowhere to store random
seeded blocks), folder names cannot and must not be encrypted the same way as the rest of the files and File names or we could potentially create folder
structure that is larger than the 255 character limit (it is still imposed in many disk formats). Folder name encryption should be therefore considered more as an
relatively strong obfuscation for humans. However one thing we made sure is that the password cannot be reversed from the encrypted folder itself.
Can you recover the password somehow?
Absolutely not, and this again goes to what was said before about the modern encryption algorithms and how they work.
The bottom line is: if you loose your password, then that’s it, there is no way to open the file or get the password back. You get a collection of files with random
noise inside and nothing else.
Encryption vs Backup
First and foremost, the proper backup is the single most important thing you need to do with your data, before even thinking about encryption.
And proper backup can be as simple as getting external disk and backing up all your video and image files, then unplugging it and storing it at a safe place. But if
you fear, for example that someone else may take the disk, then you need to think about encryption.
An encryption with MediaCryptor serves the purpose that nobody or nothing else can see that the files in question are media files or anything usable, but you can
still view them when you need to. It will likely protect you from most malware or spyware because they would not be interested in such files, it will not allow the
files be analyzed by “helpful” bots on the cloud storage, nor someone who is rampaging through your computer or sitting on the same network… but again and
again, encryption is not a matter of data “security” which is a backup.
Versioning files for NAS or Cloud backup
Interestingly, you may use the MediaCryptor Random Name encryption as a versioning system for backup to NAS or Cloud. If during Encryption you choose Fully
Randomly Generated Names and Keep Original File Data Attributes then you will be able to encrypt and store multiple copies of the same file in the same folder that
will differ only by a date (because their new encrypted file name will be all different)


Copy files, Move Files, Delete
There are few changes from normal browser. For example you can’t delete files by simply hitting Delete button in the file view mode - this has been disabled. You
can however delete files in the file view (non-thumbnail view) by simply selecting them, right click and then select delete in the popup menu. In Thumbnail view
the Delete button is enabled but it will always ask premission. Similarly you can copy and paste files from MediaCryptor to Windows File Explorer and back by
using the right click menu and Copy/Paste operations. You can also drag file out of MediaCryptor to Windows File Explorer to copy or move it there, but general
copying or moving files within MediaCryptor view and tree with drag and drop is disabled. (It is too easy to move files by accident)
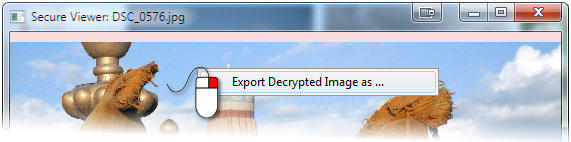
In version 3 we added export image from image viewer window (that opens after you double-click on an image). You can right click inside the image view and
then export the image into various plain (non encrypted) formats.

Create File List
(Menu-Tools). This option will create a file list text file from the encrypted folders where the original name and the encrypted name will be listed on each line. The
list will open in the internal text editor. if you want to keep it you will need to save it from within the editor.